Inside the Cookbook
- Introduction
- Understanding authentication and authorization: The foundation of app security
- Session-based authentication
- Token-based authentication
- Auth with third-party providers
- Necessity of Role-based access control (RBAC)
- Why are these important?
- Simplifying authentication and authorization with Catalyst
- Hosted Authentication
- Managing users and roles with Catalyst
- Build with Catalyst
- Conclusion
Introduction
In this guide, you’ll learn how to:
Effortlessly verify your users’ identities with smart authentication options.
Control access and permissions using simple yet powerful authorization tools.
Choose between Hosted and Embedded Authentication to fit your app’s unique needs.
Before diving in, let’s clarify a few key terms essential for app security:
Authentication: Verifying who a user, system, or entity really is before granting access.
Authorization: Determining what an authenticated user is allowed to do or access within your application.
Secure Token Management: Ensuring that once a user is authenticated, their session and credentials are handled safely, preventing unauthorized use or token theft.
You’ve built an awesome app, but do you really know who’s using it? Think of authentication as checking ID at the door it answers: “Who’s trying to get in?” Whether logging in with a username and password or signing in with Google, authentication makes sure users are who they claim to be.
Once inside, authorization decides what rooms they can enter. It answers: “What can this user do?” Maybe they can read messages but not delete them, or edit content but not manage users. Authorization sets these boundaries, keeping your app safe and organized.
If you want your app to be secure, user-friendly, and scalable without complicated code, this guide is for you. Let’s get started!
Understanding authentication and authorization: The foundation of app security
Let’s take a look at the common approaches in practice
Session-based authentication
This Stores login sessions on the server. After a user logs in, a session ID is generated and stored in a cookie on the client's side. This is common in traditional web applications (especially those using server-side rendering). The server validates the session on each request.

Token-based authentication
This often uses JWTs (JSON Web Tokens). After login, the server issues a signed token, which the client stores (usually in memory or local storage) and sends in the authorization header with each request. It's useful for stateless APIs and mobile apps and requires careful handling of token storage and expiration and refresh mechanisms.

Auth with third-party providers
Allows users to authenticate via services like Google, GitHub, or Facebook. Simplifies the login process for users, but requires more configuration (redirects, scopes, token exchange, etc.) and often uses OpenID Connect (OIDC) on top of OAuth for identity information.
Necessity of Role-based access control (RBAC)
This assigns users to roles such as “admin,” “editor,” or “viewer,” and grants permissions based on those roles. It can be combined with any of the above authentication methods to enforce access control in the application.
Why are these important?
Without authentication, anyone could use your app anonymously, leading to chaos and potential security breaches.
Without authorization, authenticated users might do things they shouldn’t like deleting data they shouldn’t access.
Together, authentication and authorization keep your app smart and secure
Simplifying authentication and authorization with Catalyst
- Implementing these systems securely from scratch is tough and time-consuming.
- Explore Catalyst by Zoho, a full stack cloud platform designed to handle these heavy lifting tasks for you.
- How Catalyst makes authentication easy:
Catalyst offers two main approaches for adding login capabilities: - Hosted Authentication
- Embedded Authentication
Managing users and roles with Catalyst
After users log in, what controls their access? Catalyst’s user roles system:
Define roles—groups of permissions, like Admin, Editor, Viewer, or custom roles you create.
Assign roles to users manually or automatically during signup.
Enforce authorization in your app by checking user roles via Catalyst SDKs.
Manage all of this easily in the Catalyst Console—no backend coding needed.
For example, your app can restrict bug deletion only to users with the Admin role, while others can only submit or view bugs.
Build with Catalyst
Build with Catalyst: QuickFix bug reporter app
Try the app live here: [QuickFix]
Imagine building QuickFix—a simple bug reporter designed for small teams.
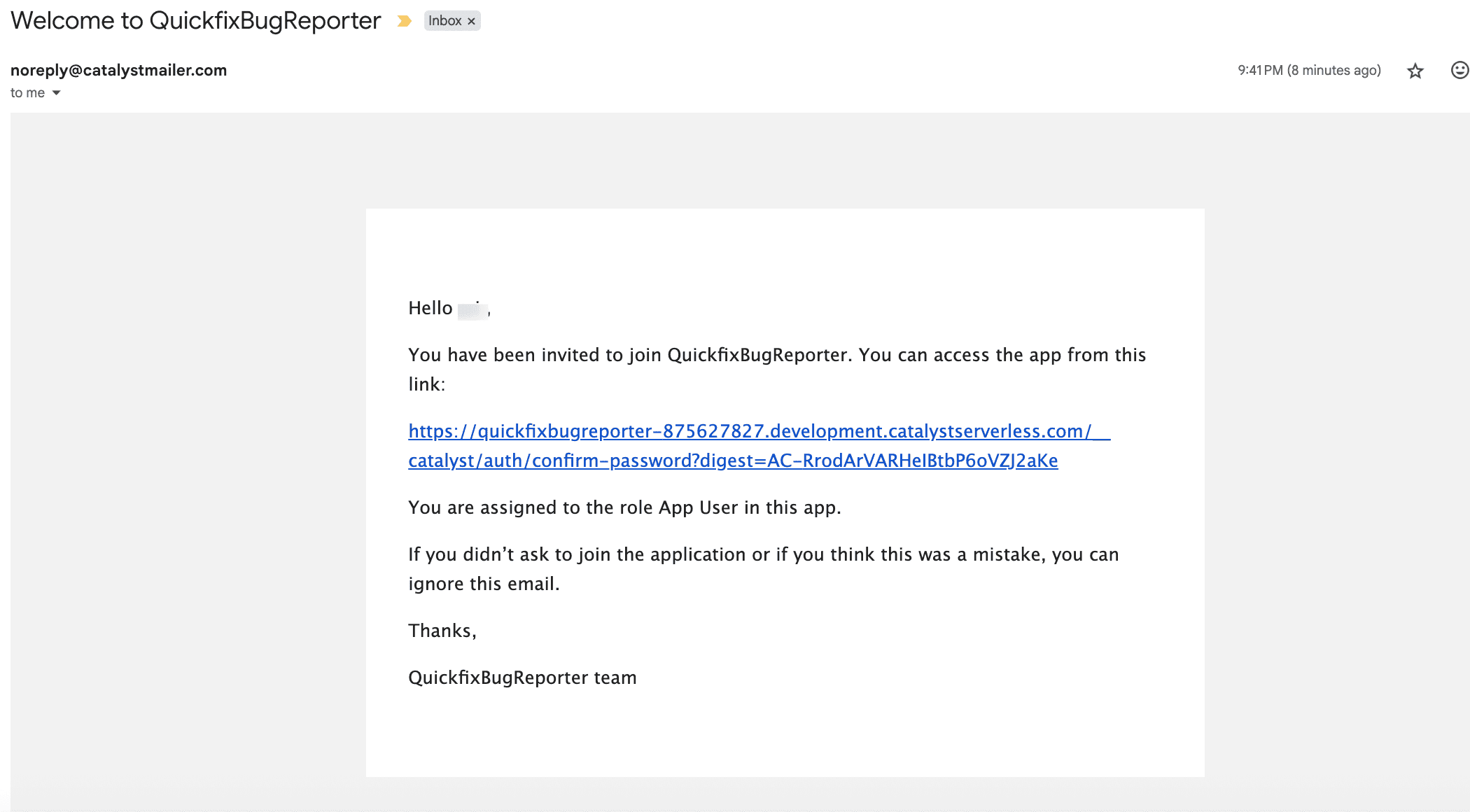
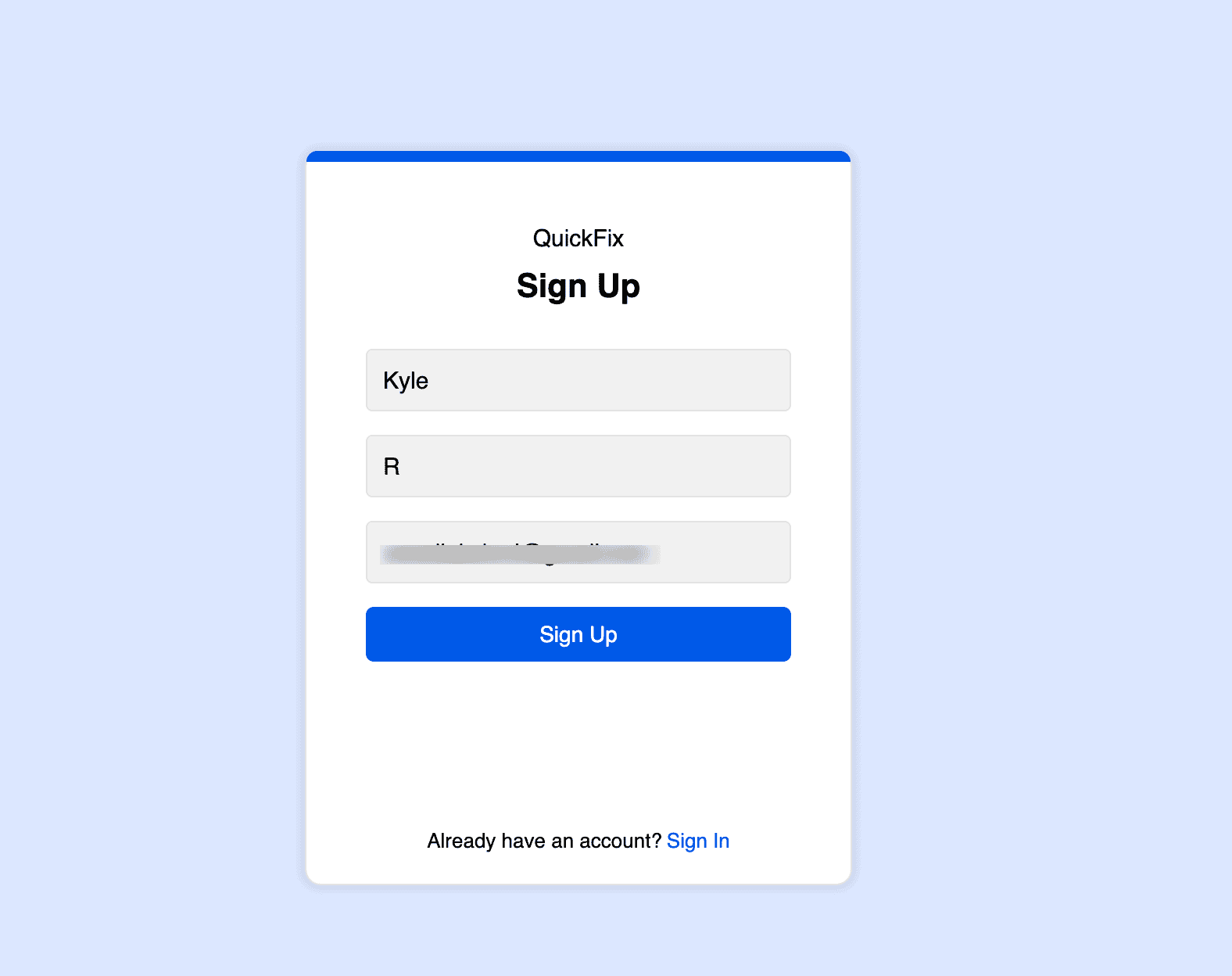
Users authenticate securely via Catalyst’s hosted login page.
Once logged in, the user’s role determines what they can see and do.
Step 1: Create a new project in Catalyst Console
Go to the Catalyst Console and create a new project called QuickFix.
Step 2: Initialize the project locally
Open your terminal and run:
Conclusion
Authentication and authorization are the backbone of secure apps. Catalyst by Zoho takes away the pain of building these systems, so you can build smarter, safer, and more robust apps faster.
Whether you want a quick hosted login or a fully embedded experience, Catalyst has you covered. And with built-in role management, your app stays secure and user-friendly.